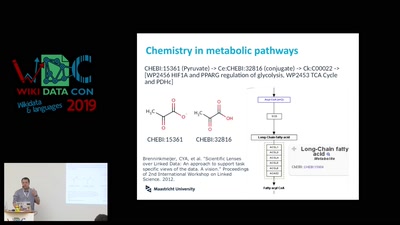
Search for "Inc.)" returned 11287 results
38 min
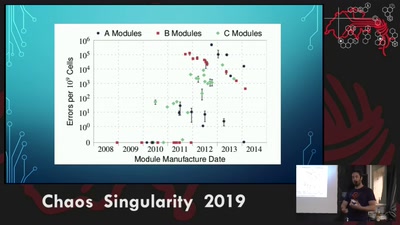
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used
45 min
Tales from Hardware Security Research
From Research over Vulnerability Discovery to Public…
20 min
Introduction to SecureShare
A peer-to-peer, end-to-end encrypted social networking…

37 min
Eliminating the database bottleneck for proper horizontal scalability
Using embeddable databases to allow true and simple…

57 min