Search for "m-1-k-3" returned 9400 results

56 min
WarGames in memory
what is the winning move?

46 min
CounterStrike
Lawful Interception

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

31 min
Demystifying Network Cards
Things you always wanted to know about NIC drivers

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…
44 min
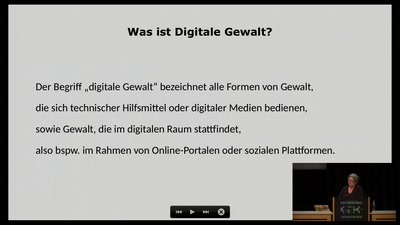
Stalking, Spy Apps, Doxing: Digitale Gewalt gegen Frauen
Die digitale Seite der häuslichen Gewalt

41 min
Frontex: Der europäische Grenzgeheimdienst
Das Grenzüberwachungssystem EUROSUR führt Aufklärungsdaten…
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

26 min
Technomonopolies
How technology is used to subvert and circumvent…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

53 min
When algorithms fail in our personal lives
Social media break up coordinator

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

62 min