Search for "big data"
prev
next

61 min
Developing the Future of Authenticated Encryption

63 min
transparency in the service of justice

32 min
Math, Functional Programming, Theorem Proving, and an…

60 min
How to drop more of your privileges to reduce attack…

28 min
One can create art and beauty with … pixels

61 min
why clearing memory is hard.
60 min
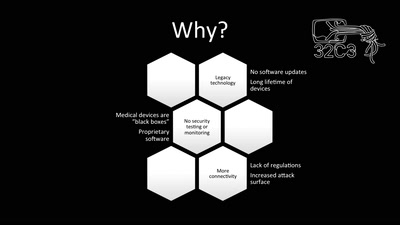
Living with a vulnerable implanted device
31 min
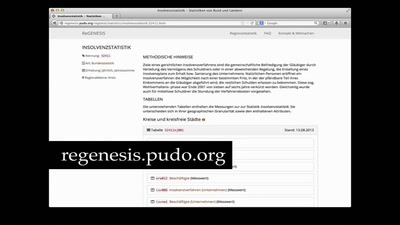
Spending a year coding in a newsroom
31 min
Why Censorship is a Bad Idea for Everyone

60 min
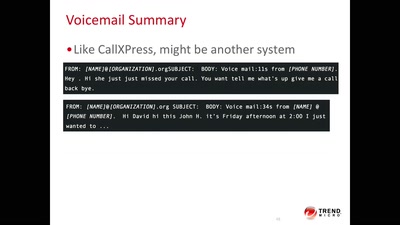
How not to do DOCSIS networks
37 min
A systemic update of sensitive information that you sniff…
60 min
Featuring the shortest movies and the largest lasers

54 min
Do you care about Matroshka processors?

66 min
A Rapidly Emerging Police State and Imminent Deportation to…

61 min
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…
38 min
Velocipedes and Face Recognition
63 min
A Strategy for for Identifying Calls for Action in Texts…
prev
next







