Search for "m-1-k-3" returned 9400 results

30 min
The ArduGuitar
An Arduino Powered Electric Guitar
35 min
Understanding millions of gates
Introduction to IC reverse engineering for…

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents
62 min
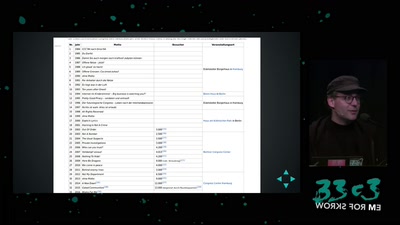
A New Kid on the Block
Conditions for a Successful Market Entry of Decentralized…
99 min
Fnord-Jahresrückblick
Wir helfen euch, die Fnords zu sehen!

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

61 min
Warum die Digitale Revolution des Lernens gescheitert ist.
Fünf Desillusionen

60 min
Windows drivers attack surface
some 'new' insights

62 min
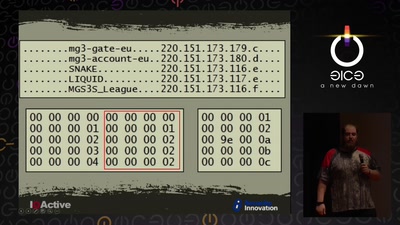
Tell no-one
A century of secret deals between the NSA and the telecom…
55 min
Cyber Necromancy
Reverse Engineering Dead Protocols

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

29 min
Perfect Paul
On Freedom of Facial Expression

25 min
»Hard Drive Punch«
Destroying data as a performative act

61 min