Search for "searchwing" returned 140 results

60 min
Adventures in Reverse Engineering Broadcom NIC Firmware
Unlocking a system with 100% open source firmware

56 min
Viva la Vita Vida
Hacking the most secure handheld console

43 min
Tractors, Rockets and the Internet in Belarus
How belarusian authoritarian regime is using technologies…
40 min
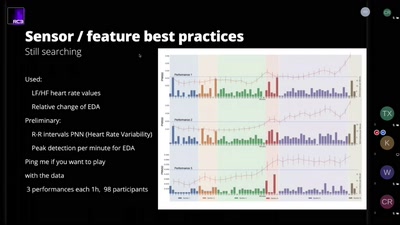
Boiling Mind
Analysing the link between audience physiology and…
47 min
Democratizing and Decolonizing the Future
Grassroots Utopias from Indonesia

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…
41 min
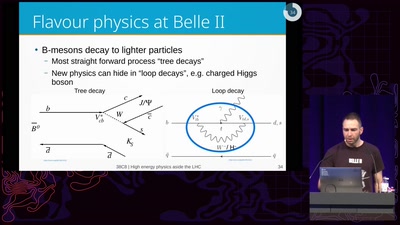
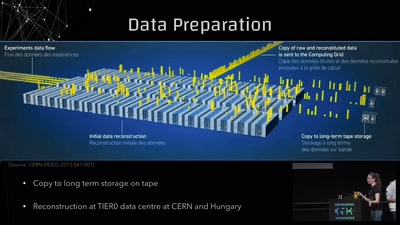
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

55 min
Attribution revolution
Turning copyright upside-down with metadata

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data
46 min
The Mission of the MV Louise Michel
"Feminism will be anti-racist or it won´t be"

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

60 min