Search for "crypto wars" returned 318 results
47 min
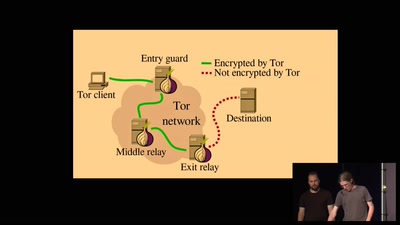
Introduction to Mix Networks and Katzenpost
a new anonymity movement
69 min
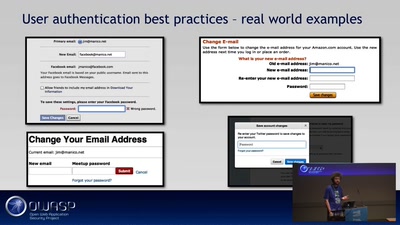
OWASP ProActive Controls
Sichere Anwendungen erstellen?
62 min
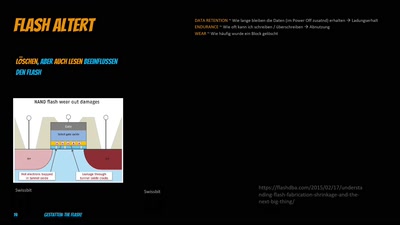
Gestatten: The Flash
Security von Embedded Systemen pimpen - Wieso? Weshalb? Wow!

59 min
Security Evaluation of Russian GOST Cipher
Survey of All Known Attacks on Russian Government…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

55 min