Search for "ths" returned 8780 results

74 min
Legal, illegal, decentral: Post-hacker-ethics cyberwar
Applied loss of control to hacker-ethics?
56 min
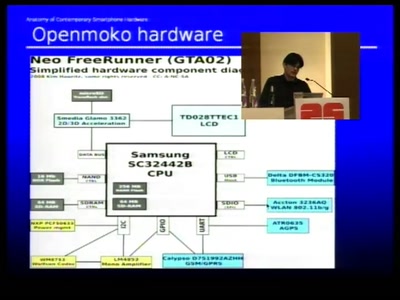
Anatomy of smartphone hardware
Dissecting contemporary cellphone hardware
69 min
OWASP ProActive Controls
Sichere Anwendungen erstellen?
48 min
GPS-Trackers
How they track you when your mobile is switched off

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

46 min
Automated Exploit Detection in Binaries
Finding exploitable vulnerabilities in binaries
31 min
Smart ways to monitor your Linux systems using open source software
Modern open source software monitoring techniques
37 min
Reverse-Engineering DisplayLink devices
USB to DVI for Hackers
58 min