Search for "m-1-k-3" returned 9397 results
63 min
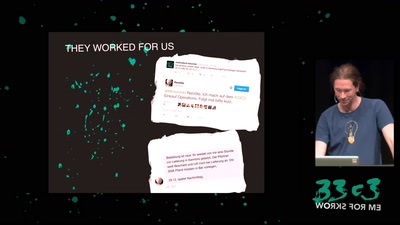
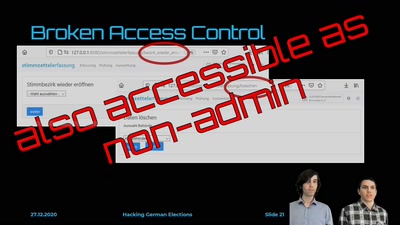
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…

55 min
The DROWN Attack
Breaking TLS using SSLv2

29 min