Search for "HItc" returned 389 results

45 min
To Protect And Infect
The militarization of the Internet
59 min
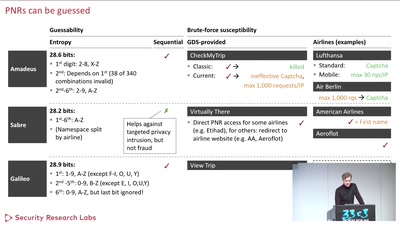
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches
53 min
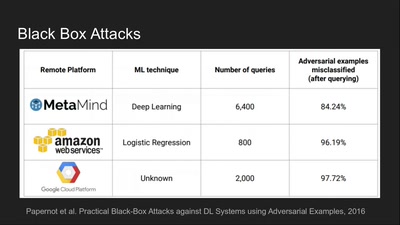
Deep Learning Blindspots
Tools for Fooling the "Black Box"

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…
52 min
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

63 min