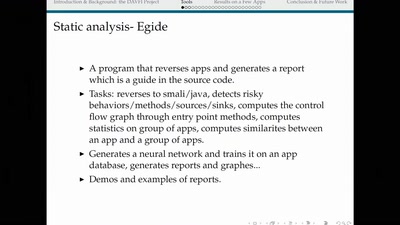
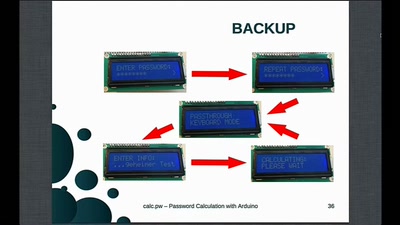
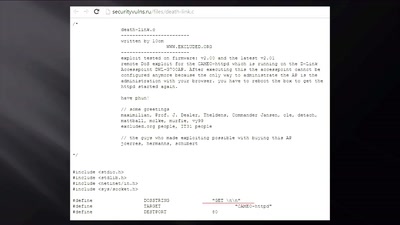
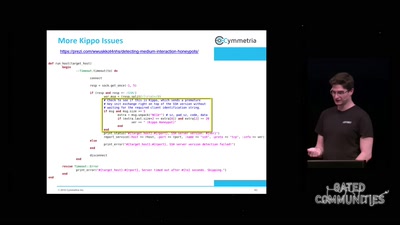
Search for "SS7" returned 396 results

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…
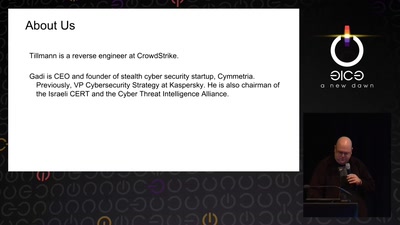
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine
60 min
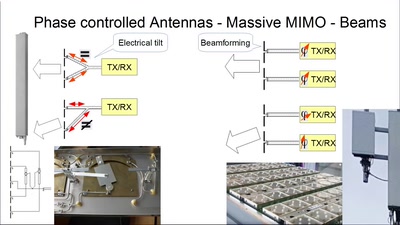
Der Pfad von 4G zu 5G
Die Luftschnittstelle und das Core im Wandel der Zahlen

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

38 min
Gerechtigkeit 4.0
Makroökonomische Auswirkungen der Digitalisierung auf den…

20 min
Mastering the Maze
Unleashing Reinforcement Learning in Penetration Testing…

62 min
To Protect And Infect, Part 2
The militarization of the Internet
47 min