Search for person "Walter van Host" returned 139 results

44 min
Life Needs Internet
Documenting digital culture through handwritten letters
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

42 min
A world without blockchain
How (inter)national money transfers works

53 min
Smart, safe & happy
ensuring civil rights in the digital era

27 min
Detecting a breach from an attackers perspective.
We're gonna regret this
58 min
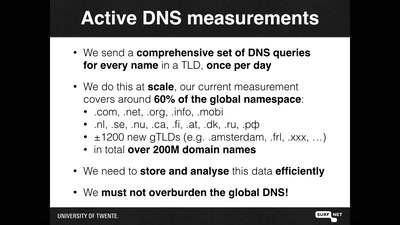
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this

60 min
Flip Feng Shui
Advanced Rowhammer exploitation on cloud, desktop, and…

53 min
TBM: Trusted boot module
NLNet sponsored (open hardware) trusted boot module

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

60 min
Windows drivers attack surface
some 'new' insights

45 min
Time affects
Human-computer-synchronizations

28 min