Search for "16" returned 4642 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools
61 min
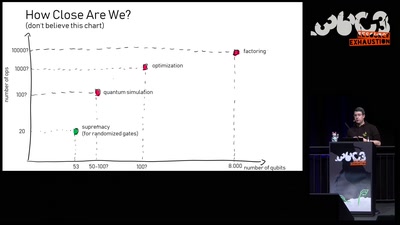
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

66 min
Keine Anhaltspunkte für flächendeckende Überwachung
Die Diskussion um NSA, PRISM, Tempora sprachlich und…

58 min
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…
39 min
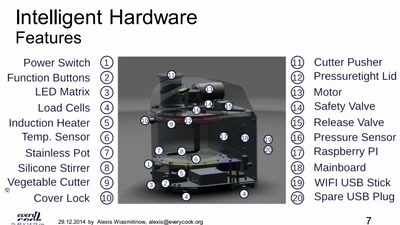
Why do we need an open food information platform
We want all data about food to be linked and public

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

54 min