Search for "15" returned 4954 results

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
46 min
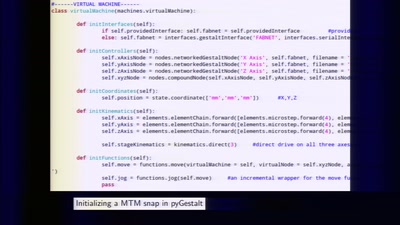
Making machines that make
rapid prototyping of digital fabrication and…

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

59 min
Security of the IC Backside
The future of IC analysis
61 min
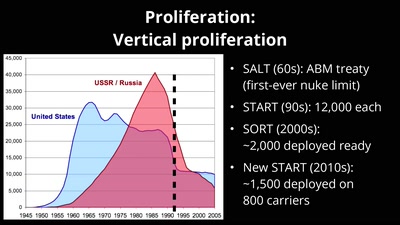
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
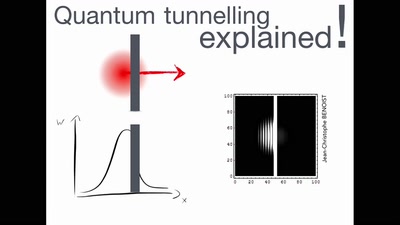
Quantum Cryptography
from key distribution to position-based cryptography

64 min
ES GIBT VIEL ZU TUN - HAU'N WIR AB.
[Die Untersuchung]

51 min