Search for "30" returned 4243 results

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

32 min
Die Sprache der Überwacher
Wie in Österreich über Sicherheit und Überwachung…

33 min
UPSat - the first open source satellite
Going to space the libre way

115 min
Hacker Jeopardy
Zahlenraten für Geeks

58 min
Die Krise der Bilder ist die Krise der Politik
Die Krise der Politik ist die Krise der Bilder
62 min
SuperMUC-NG
… und das Rennen um den schnellsten Computer der Welt

53 min
When algorithms fail in our personal lives
Social media break up coordinator

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

58 min
Virtual Machine Introspection
From the Outside Looking In

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…
35 min
YOUR DATA MIRROR
Wie die Macht der Daten die Demokratie untergräbt

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…
35 min
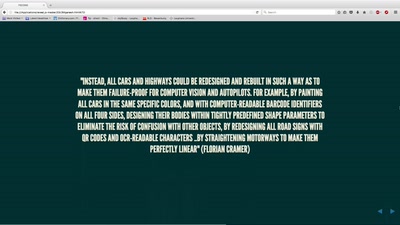
Ethics in the data society
Power and politics in the development of the driverless car
35 min
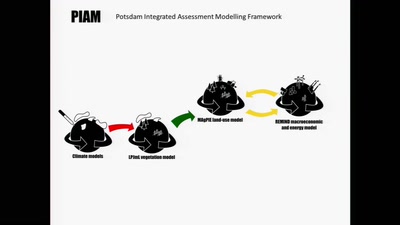
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…
91 min