Search for "27" returned 4133 results
57 min
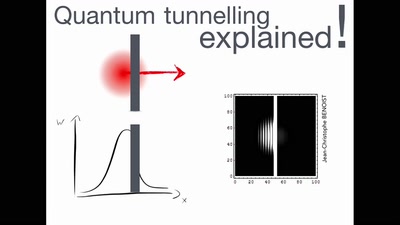
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
46 min
Making machines that make
rapid prototyping of digital fabrication and…

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3

60 min
Quantum Cryptography
from key distribution to position-based cryptography

59 min
Security of the IC Backside
The future of IC analysis
20 min
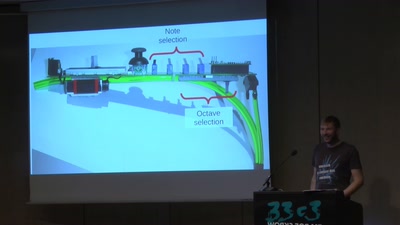
The Nibbletronic
A DIY MIDI Controller and a New UI for Wind Instruments

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP
61 min
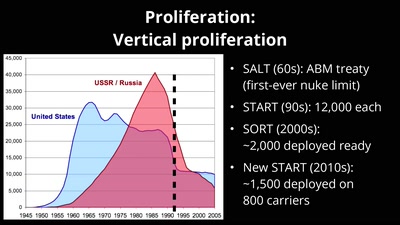
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

55 min
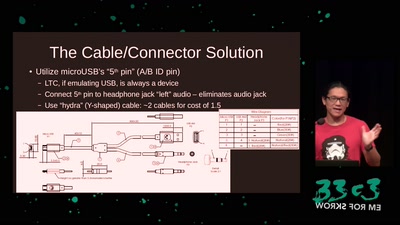
The Gospel of IRMA
Attribute Based Credentials in Practice
56 min