Search for "15" returned 4797 results

55 min
What is Good Technology?
Answers & practical guidelines for engineers.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

60 min
Beyond your cable modem
How not to do DOCSIS networks
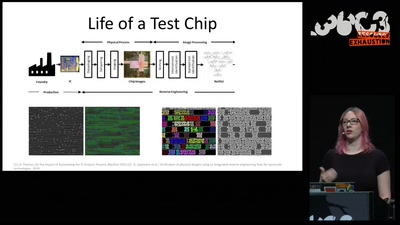
35 min
Understanding millions of gates
Introduction to IC reverse engineering for…

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

61 min
Quantenphysik und Kosmologie
Eine Einführung für blutige Anfänger

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

32 min