Search for "15" returned 4915 results

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
Concepts for global TSCM
getting out of surveillance state mode
40 min
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

55 min
White-Box Cryptography
Survey
38 min
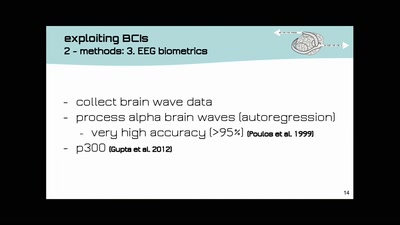
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

40 min
Radical Digital Painting
Fantastic Media Manipulation
32 min
library operating systems
reject the default reality^W abstractions and substitute…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

58 min
When hardware must „just work“
An inside look at x86 CPU design

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?
50 min