Search for "15" returned 4784 results

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

61 min
Nintendo Hacking 2016
Game Over

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks
61 min
Damn Vulnerable Chemical Process
Exploitation in a new media
59 min
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees
30 min
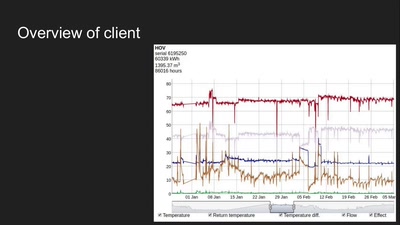
“Nabovarme” opensource heating infrastructure in Christiania
Freetown Christiania´s digitally controlled/surveyed…

62 min
To Protect And Infect, Part 2
The militarization of the Internet

43 min
Repair-Cafés
… und warum ihr dabei mitmachen solltet
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…
35 min
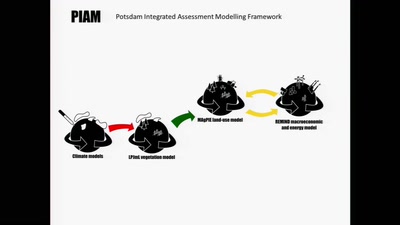
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

62 min
Was schützt eigentlich der Datenschutz?
Warum DatenschützerInnen aufhören müssen von individueller…

31 min
TrustZone is not enough
Hijacking debug components for embedded security

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

95 min
The Time is Right
Ein Science-Fiction-Theaterstück

65 min