Search for "12" returned 5000 results
60 min
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders

60 min
Shopshifting
The potential for payment system abuse
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

55 min
The DROWN Attack
Breaking TLS using SSLv2

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
60 min
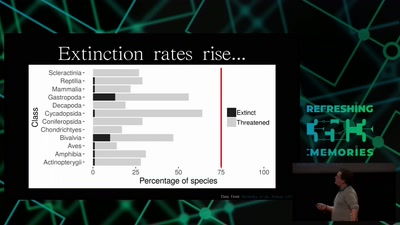
Hacking Ecology
How Data Scientists can help to avoid a sixth global…
63 min
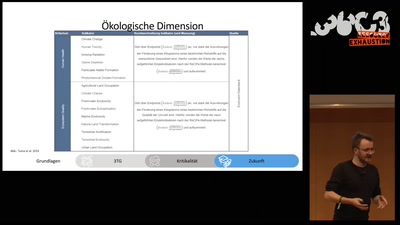
Kritikalität von Rohstoffen - wann platzt die Bombe?
Ein nicht nuklearer Blick auf das Ende der Welt

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

60 min
Are machines feminine?
exploring the relations between design and perception of…

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
58 min