Search for "20" returned 4812 results

51 min
Funky File Formats
Advanced binary tricks

58 min
Open Source Estrogen
From molecular colonization to molecular collaboration

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…
58 min
Hacking how we see
A way to fix lazy eye?

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

24 min
The Four Wars
Terror, whistleblowers, drugs, internet

58 min
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…
47 min
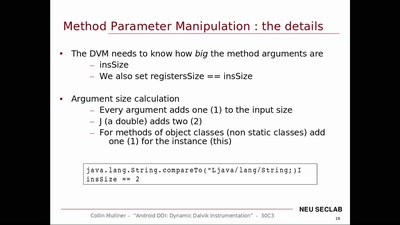
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

60 min
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…

101 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
55 min