Search for "13" returned 4820 results

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

43 min
Microtargeting und Manipulation
Von Cambridge Analytica zur EU-Wahl

60 min
Dieselgate – A year later
env stinks || exit
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet
32 min
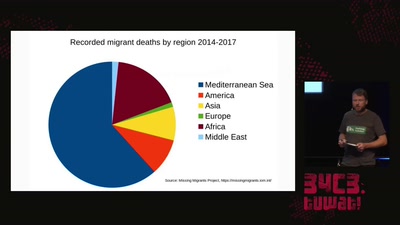
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

60 min
Vor Windows 8 wird gewarnt
Und nichts (Secure) Bootet mehr?

46 min
CounterStrike
Lawful Interception
37 min
Wie der kleine Basti die Welt erobern wollte und was dabei schiefging. Eine Moritat aus…
"Es wird nicht ohne hässliche Bilder gehen"

30 min
apertus° AXIOM
The first Open Source Cinema Camera

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

29 min
Es sind die kleinen Dinge im Leben II
was alles geht und wie man anfängt, mit Mikroskopen

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

46 min







