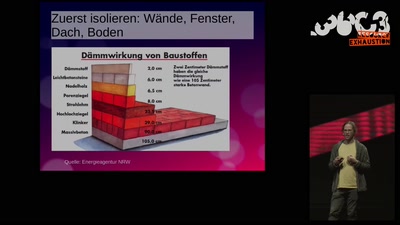
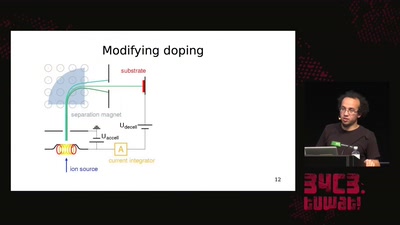
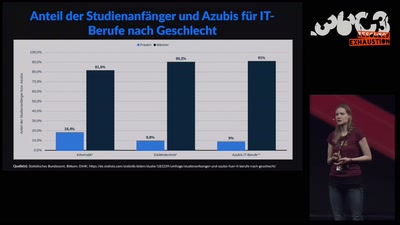
Search for "20" returned 4647 results

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session
61 min
Projekt Hannah
Ein open-source Hardware- und Software-Design für…
58 min
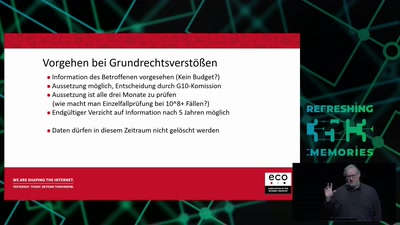
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…
32 min
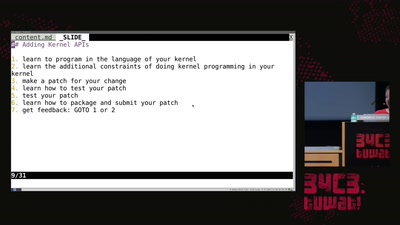
library operating systems
reject the default reality^W abstractions and substitute…

63 min
Reconstructing narratives
transparency in the service of justice

54 min
World War II Hackers
Stalin's best men, armed with paper and pen
60 min
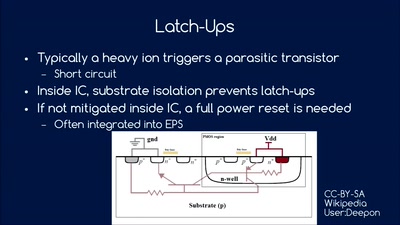
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

64 min