Search for "25" returned 4424 results

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI
62 min
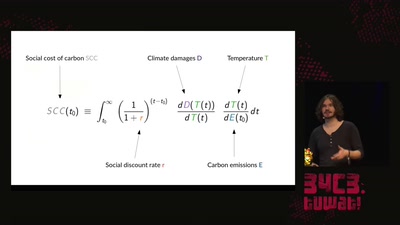
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

42 min
Hackerparagraph § 202c StGB // Reality Check
Cybercrime-Ermittlungen: Vorsicht vor der Polizei! Oder:…
59 min
Internet of Fails
Where IoT has gone wrong

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…
61 min