Search for "51" returned 3738 results
57 min
Hello World!
How to make art after Snowden?

58 min
PLC-Blaster
Ein Computerwurm für PLCs

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…
60 min
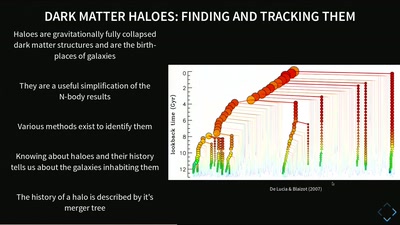
Simulating Universes
What Virtual Universes Can Tell Us About Our Own
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine

60 min
Lets break modern binary code obfuscation
A semantics based approach

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

62 min
radare demystified
after 1.0

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

53 min
From Maxwell to antenna arrays
How 150 year old equations still help to communicate

60 min



![TVLuke: Baumbilanzen befreien [FreiTalk N8]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1377-a1d32bbd-7f47-4a9f-83dd-c2e62d1f67f9.jpg)