Search for "50" returned 3731 results

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …

58 min
Baseband Exploitation in 2013
Hexagon challenges
62 min
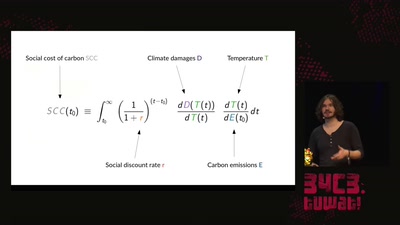
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

58 min
When hardware must „just work“
An inside look at x86 CPU design

63 min
goto fail;
exploring two decades of transport layer insecurity

61 min