Search for "12" returned 5156 results

59 min
Security of the IC Backside
The future of IC analysis

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

60 min
Dieselgate – A year later
env stinks || exit

58 min
PLC-Blaster
Ein Computerwurm für PLCs

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…
61 min
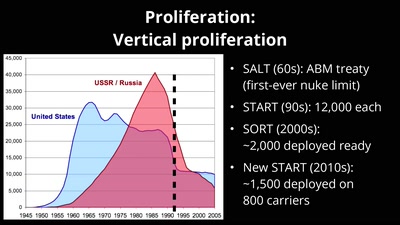
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

60 min
Vor Windows 8 wird gewarnt
Und nichts (Secure) Bootet mehr?

60 min
Quantum Cryptography
from key distribution to position-based cryptography

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
apertus° AXIOM
The first Open Source Cinema Camera

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

62 min