Search for "12" returned 5141 results

50 min
Connected Mobility hacken: digital.bike.23
Von E-Bikes in der Connected Mobility zur Entstehung eines…

55 min
The DROWN Attack
Breaking TLS using SSLv2
31 min
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…

29 min
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...
37 min
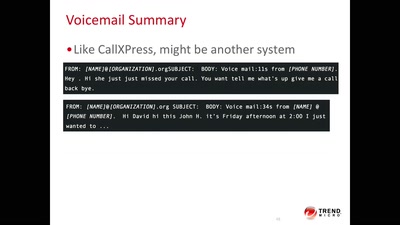
Code BROWN in the Air
A systemic update of sensitive information that you sniff…

60 min
A Story of Discrimination and Unfairness
Prejudice in Word Embeddings

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

44 min
ASLR on the line
Practical cache attacks on the MMU
32 min
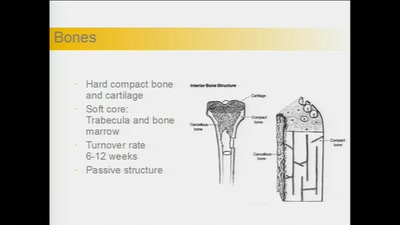
Coding your body
How to decipher the messages of your body
63 min
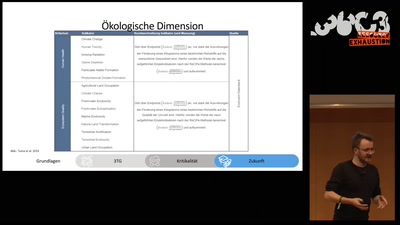
Kritikalität von Rohstoffen - wann platzt die Bombe?
Ein nicht nuklearer Blick auf das Ende der Welt

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study
32 min