Search for "20" returned 4644 results

36 min
Modchips of the State
Hardware implants in the supply-chain

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…
35 min
hacking disaster
mit Krisenintervention den Kapitalismus hacken

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
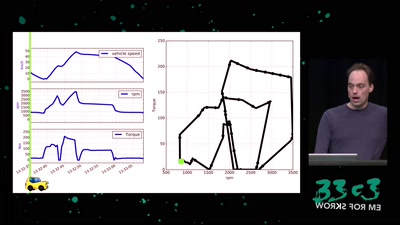
60 min
Software Defined Emissions
A hacker’s review of Dieselgate

43 min
This is NOT a proposal about mass surveillance!
Analysing the terminology of the UK’s Snooper’s Charter

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet
63 min
Das Assange-Auslieferungsverfahren
Als Prozessbeobachter in London

61 min