Search for "18" returned 4654 results

60 min
Von Kaffeeriechern, Abtrittanbietern und Fischbeinreißern
Berufe aus vergangenen Zeiten
62 min
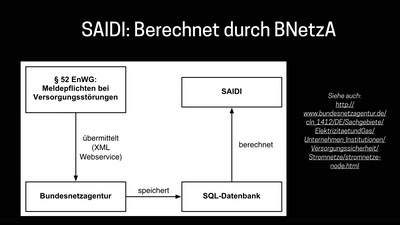
Wie man einen Blackout verursacht
und warum das gar nicht so einfach ist.

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

32 min
History and implications of DRM
From tractors to Web standards

72 min
Console Hacking
Breaking the 3DS

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
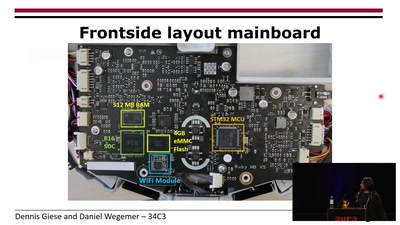
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

58 min
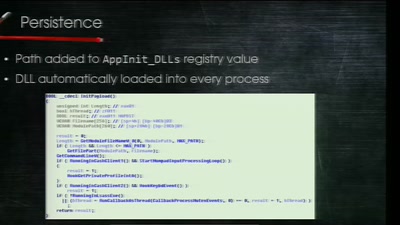
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware

59 min
Provable Security
How I learned to stop worrying and love the backdoor

61 min