Search for "31" returned 4039 results

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

42 min
A world without blockchain
How (inter)national money transfers works
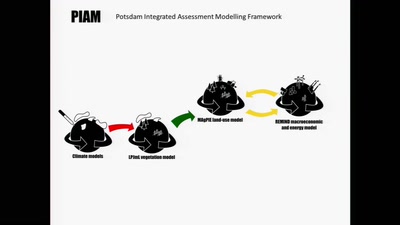
35 min
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…
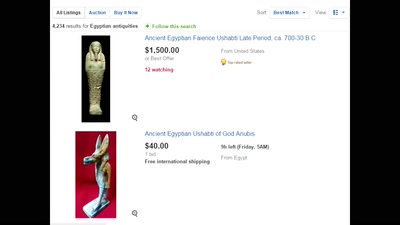
56 min
The mummy unwrapped
Cultural Commons durch Kunstraub
54 min
"Day 2 Ops" Linux for Kubernetes and Container Workloads
Leveraging 10 years of Container Linux experience for…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
58 min
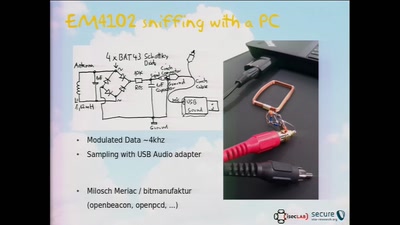
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende
61 min
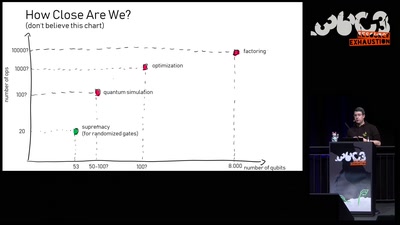
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research

66 min