Search for "19" returned 4627 results
60 min
Die verborgene Seite des Mobilfunks
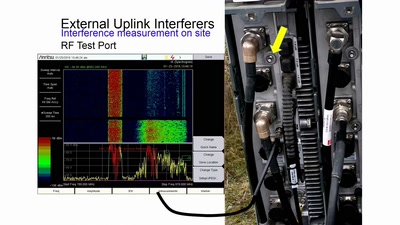
HF-Störquellen im Uplink

48 min
Seidenstraße
The Making of…
21 min
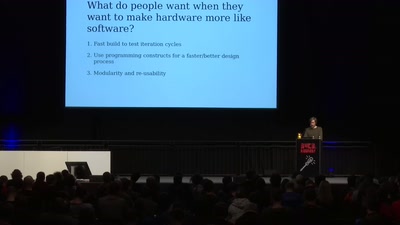
Designing PCBs with code
Is designing circuits with code instead of CAD the future…

58 min
Switches Get Stitches
Industrial System Ownership

45 min
To Protect And Infect
The militarization of the Internet

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

32 min
The Case for Scale in Cyber Security
Security Track Keynote

31 min
Extended DNA Analysis
Political pressure for DNA-based facial composites

30 min