Search for "15" returned 4794 results

30 min
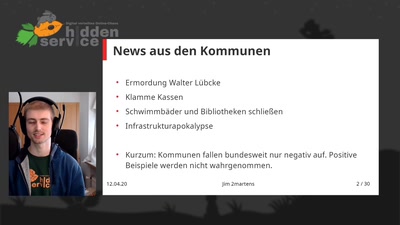
Science is broken
How much can we trust science in light failed replications,…

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures

32 min
Think big or care for yourself
On the obstacles to think of emergent technologies in the…

58 min
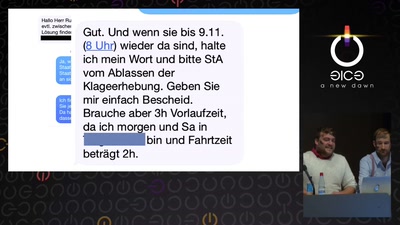
Switches Get Stitches
Industrial System Ownership
67 min
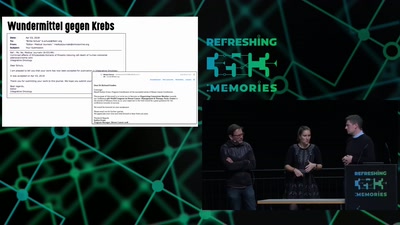
Mit Kunst die Gesellschaft hacken
Das Zentrum für politische Schönheit

55 min
What is Good Technology?
Answers & practical guidelines for engineers.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

60 min
Beyond your cable modem
How not to do DOCSIS networks
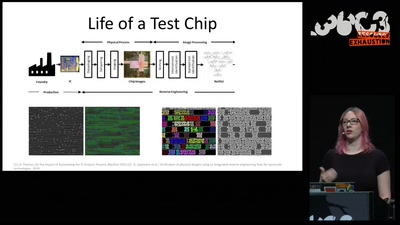
35 min
Understanding millions of gates
Introduction to IC reverse engineering for…

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

56 min