Search for "15" returned 4784 results

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

62 min
HUMUS sapiens
Open Soil Research
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

32 min
History and implications of DRM
From tractors to Web standards

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
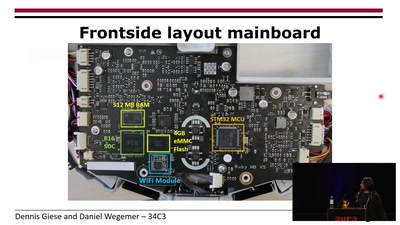
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

72 min
Console Hacking
Breaking the 3DS

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…

59 min