Search for "28" returned 4264 results

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

60 min
Stromtankstellen – eine neue öffentliche Infrastruktur
Was kann das? Wie kann ich das nutzen? Wo besteht…

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…
33 min
Digitale Bildung in der Schule
5.-Klässlerinnen, die über die Millisekunden für einen…
38 min
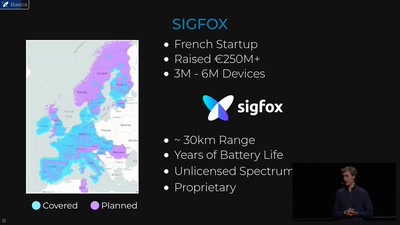
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…

28 min
Home Distilling
Theory and practice of moonshining and legal distilling

61 min
QualityLand
Lesung

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
36 min
Long Distance Quantum Communication
Concepts and components for intercontinal communication…
41 min
SCADA StrangeLove 2
We already know
58 min
Energiespeicher von heute für die Energie von morgen
Wohin eigentlich mit all der erneuerbaren Energie?
40 min



![Resistance against dictatorship in Belarus in times of war [EN]](https://static.media.ccc.de/media/events/datenspuren/2024/463-72bfad55-bbd5-5dad-9a8f-9109ed64b787.jpg)