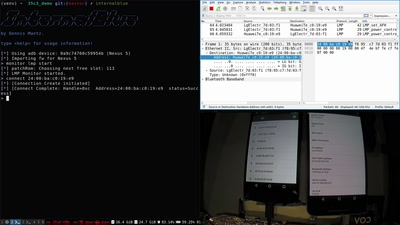
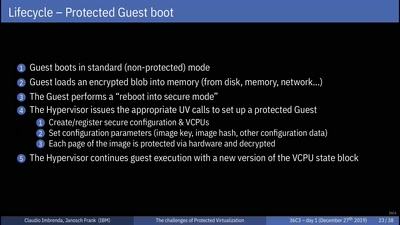
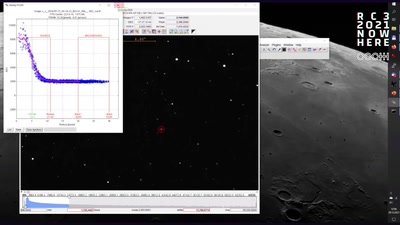
Search for "31" returned 4036 results

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3
32 min
library operating systems
reject the default reality^W abstractions and substitute…

30 min
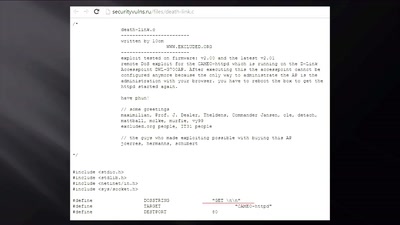
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches
40 min
Court in the Akten
OpenSchufa und OffeneGesetze
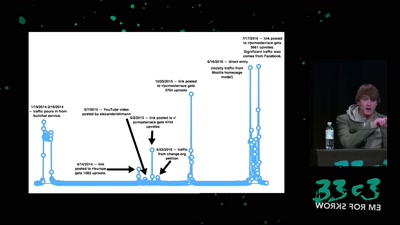
31 min
Make the Internet Neutral Again
Let's put the new EU Net Neutrality rules to work

55 min
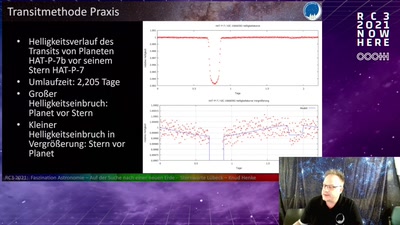
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

54 min
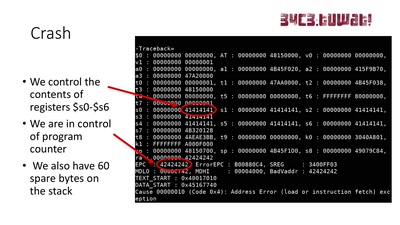
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

30 min


![failed: [Inklusion]](https://static.media.ccc.de/media/conferences/divoc/r2r/7-28904449-d357-566f-97ef-86ade89f9395.jpg)