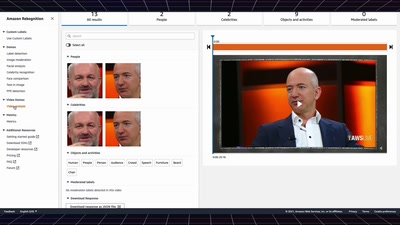
Search for "25" returned 4553 results
36 min
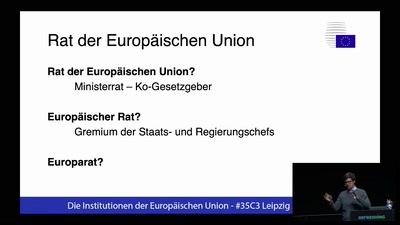
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

107 min
Nougatbytes 11₂
Die geekige Wort- & Bilderrätselspielshau ist zuЯück

59 min
Provable Security
How I learned to stop worrying and love the backdoor
60 min
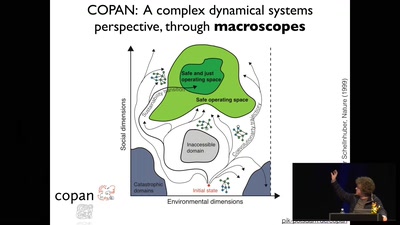
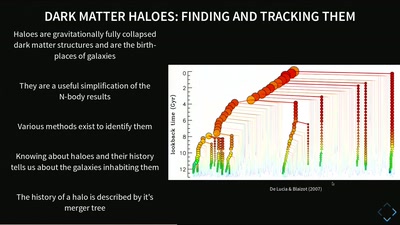
Simulating Universes
What Virtual Universes Can Tell Us About Our Own
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

32 min
History and implications of DRM
From tractors to Web standards

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
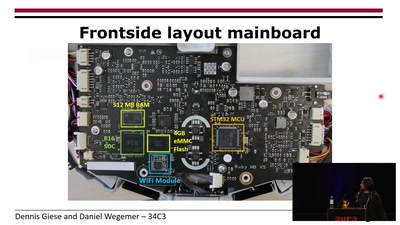
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

62 min
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…

60 min