Search for "19" returned 4468 results
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

59 min
Security of the IC Backside
The future of IC analysis
58 min
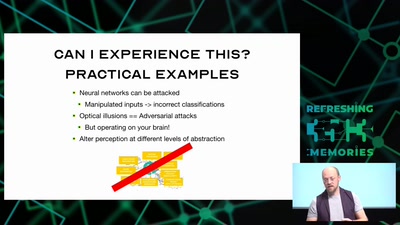
Hacking how we see
A way to fix lazy eye?

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

58 min
Baseband Exploitation in 2013
Hexagon challenges

58 min
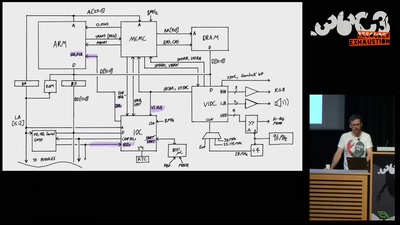
When hardware must „just work“
An inside look at x86 CPU design

55 min
White-Box Cryptography
Survey

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

63 min
goto fail;
exploring two decades of transport layer insecurity

62 min