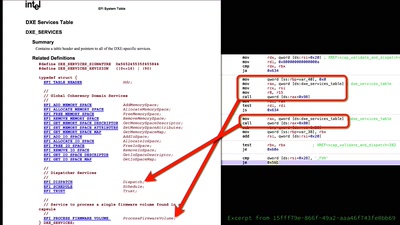
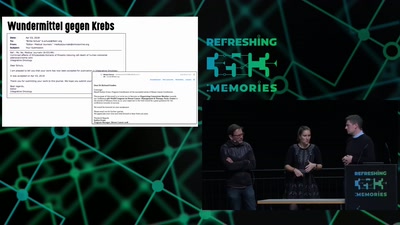
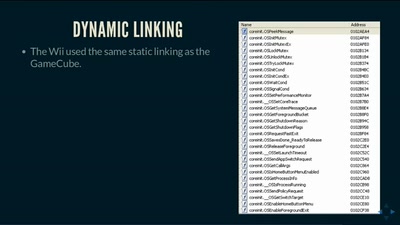
Search for "Privacy" returned 821 results

63 min
Reconstructing narratives
transparency in the service of justice

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

61 min
Programming FPGAs with PSHDL
Let's create the Arduino for FPGAs
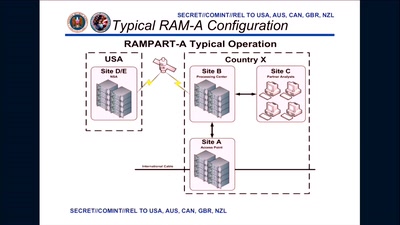
64 min
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
62 min
Public Library/Memory of the World
Access to knowledge for every member of society

58 min