Search for "20c3" returned 3916 results

44 min
Open Source Machine Translation
From tools, to tricks, to projects: build a translation…
65 min
Overtaking Proprietary Software Without Writing Code
"a few rough insights on sharpening free software"
66 min
KinectFusion
Real-time 3D Reconstruction and Interaction Using a Moving…
52 min
Void the warranty!
How to start analyzing blackboxes

51 min
Apple vs. Google Client Platforms
How you end up being the Victim.

48 min
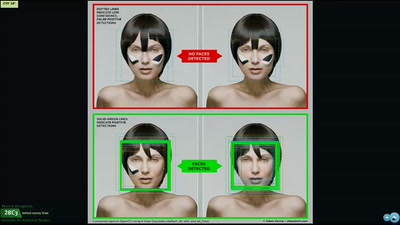
SWF and the Malware Tragedy
Hide and Seek in A. Flash
60 min
Macro dragnets: Why trawl the river when you can do the whole ocean
What happens when data collection goes awry in the 21st…

52 min
Lieber Cyborg als Göttin
Politischer Hacktivismus und Cyborgfeminismus

58 min
How to squeeze more performance out of your wifi
Cross-layer optimization strategies for long-range IEEE…
51 min
Lightning Talks Day2
4 minutes of fame

45 min
Privacy in the social semantic web
Social networks based on XMPP
54 min
Datamining for Hackers
Encrypted Traffic Mining

64 min
„Die Koalition setzt sich aber aktiv und ernsthaft dafür ein“
Sprachlicher Nebel in der Politik

65 min
Quantified-Self and OpenBCI Neurofeedback Mind-Hacking
Transhumanism, Self-Optimization and Neurofeedback for…

46 min
Paper-Prototyping Workshop
Eine Usability-Methode

59 min
Vulnerability markets
What is the economic value of a zero-day exploit?

67 min