56 min
Console Hacking 2008: Wii Fail
Is implementation the enemy of design?
61 min
The Ultimate Commodore 64 Talk
Everything about the C64 in 64 Minutes

61 min
MD5 considered harmful today
Creating a rogue CA Certificate

61 min
Handschellen hacken
Essentielles Grundwissen für alle, die nichts zu verbergen…

61 min
Der Hackerparagraph 202c StGB
Bestandsaufnahme und Auswirkungen
94 min
Security Nightmares 2009
Oder: worüber wir nächstes Jahr lachen werden

76 min
Messing Around with Garage Doors
Breaking Remote Keyless Entry Systems with Power Analysis
58 min
Advanced memory forensics: The Cold Boot Attacks
Recovering keys and other secrets after power off

37 min
Cracking the MSP430 BSL
Part Two
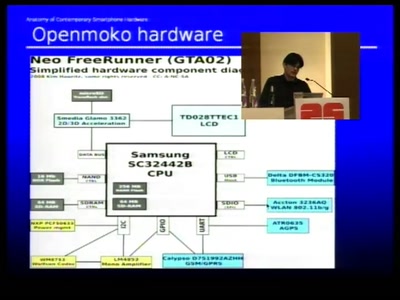
56 min
Anatomy of smartphone hardware
Dissecting contemporary cellphone hardware
50 min
FAIFA: A first open source PLC tool
PowerLineCommunications has now their open source tool
58 min
Hacking the iPhone
Pwning Apple's Mobile Internet Device
48 min
Full-Disk-Encryption Crash-Course
Everything to hide

44 min
OnionCat – A Tor-based Anonymous VPN
Building an anonymous Internet within the Internet

65 min
Blinkenlights Stereoscope
Behind the scenes of the new light installation
66 min
Cisco IOS attack and defense
The State of the Art

82 min
Attacking NFC mobile phones
First look at the security of NFC mobile phones
63 min
Banking Malware 101
Overview of Current Keylogger Threats
46 min
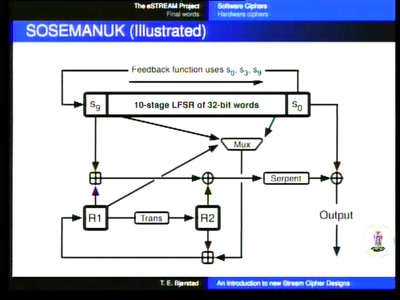
An introduction to new stream cipher designs
Turning data into line noise and back

62 min
Security and anonymity vulnerabilities in Tor
Past, present, and future
30 min
TCP Denial of Service Vulnerabilities
Accepting the Partial Disclosure Challenge

50 min
coreboot: Beyond The Final Frontier
Open source BIOS replacement with a radical approach to…

50 min
Predictable RNG in the vulnerable Debian OpenSSL package
the What and the How

58 min
Security Failures in Smart Card Payment Systems
Tampering the Tamper-Proof
35 min
Tricks: makes you smile
A clever or ingenious device or expedient; adroit…

61 min
Attacking Rich Internet Applications
Not your mother's XSS bugs
63 min
Exploiting Symbian
Symbian Exploit and Shellcode Development

92 min
Security Nightmares 2009 (English interpretation)
Or: about what we will laugh next year

48 min
Vertex Hacking
Reverse Engineering von 3D-Dateiformaten

48 min
SWF and the Malware Tragedy
Hide and Seek in A. Flash

53 min
Short Attention Span Security
A little of everything

38 min