Search for "157" returned 2502 results
62 min
Wie man einen Blackout verursacht
und warum das gar nicht so einfach ist.
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

62 min
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…
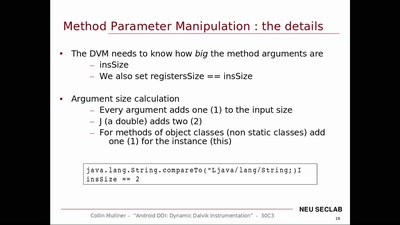
47 min
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators
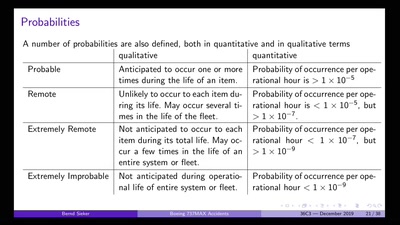
60 min
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system

70 min
Security Nightmares 0x14
Was Sie schon immer nicht über darüber wissen wollten wer…

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…

101 min
Chaos Communication Slam
Technische Liebesgedichte & Horrorgeschichten im…

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology
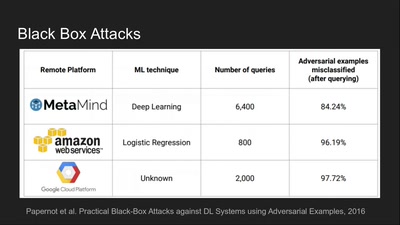
53 min
Deep Learning Blindspots
Tools for Fooling the "Black Box"

62 min
Netzpolitik in der Schweiz 2016
Grundrechte per Volksentscheid versenken

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

55 min