Search for ".uje" returned 3063 results

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

63 min
goto fail;
exploring two decades of transport layer insecurity
42 min
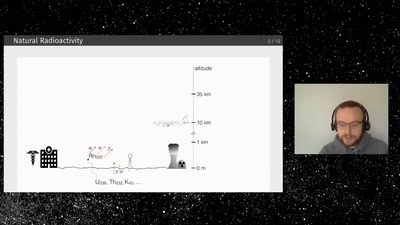
Measuring radioactivity using low-cost silicon sensors
A DIY particle physics detector in a tin box.

61 min
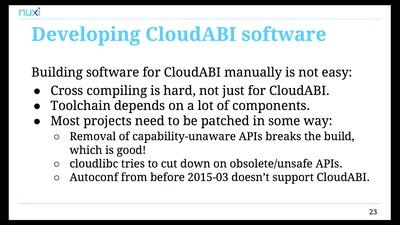
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…
65 min
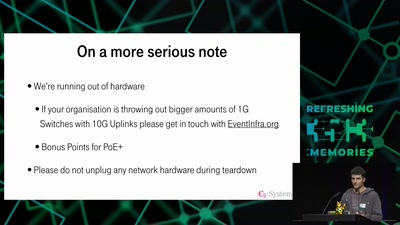
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society

59 min
Security of the IC Backside
The future of IC analysis
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…
31 min
DPRK Consumer Technology
Facts to fight lore
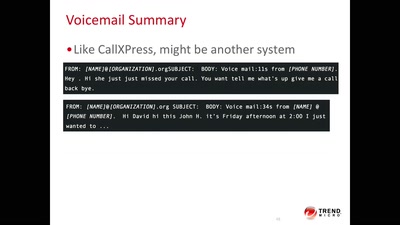
37 min
Code BROWN in the Air
A systemic update of sensitive information that you sniff…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

55 min