Search for "16164" returned 550 results

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…
113 min
Das Bits&Bäume-Sporangium
8 Mikrokosmen, 8 Expert*innen, je 8 Minuten zu…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

62 min
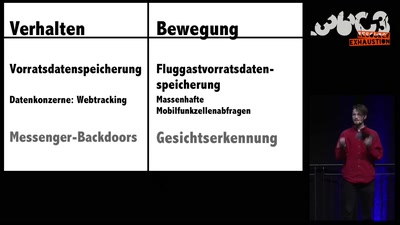
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

60 min
Concepts for global TSCM
getting out of surveillance state mode

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
When hardware must „just work“
An inside look at x86 CPU design

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
58 min
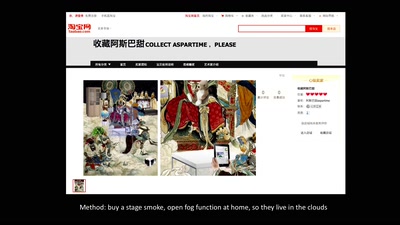
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

101 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3
58 min
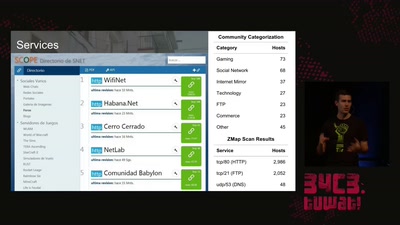
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…
62 min
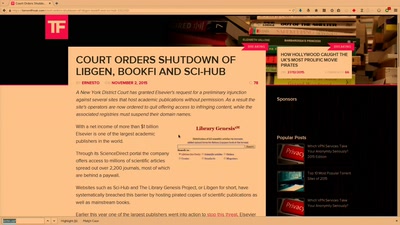
Public Library/Memory of the World
Access to knowledge for every member of society

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

58 min





