Search for "tor" returned 9959 results
41 min
Frënn vun der Ënn
Betreiben von Tor-Relays als Organisation
55 min
Modular Web
New ways for free software developers to shape the world.

26 min
Hacking the World
The struggle for security for all.

49 min
MySQL Multi-Master Replication Failover - A step-by-step explanation
How to setup a MySQL cluster with Automatic failover for HA
58 min
Torservers.net
Geschichten über den Betrieb von Tor Exit Relays

32 min
Live: Avahi / Zeroconf: Some magic sauce that's about more than files and printers
Hand editing config files for local deployment? Say hi to…

11 min
Lightning Talks
Free for all :)
68 min
Rocket propulsion basics
An introduction to rocket engines and their application for…

49 min
Syscall proxying fun and applications
Introduction to syscall proxying and applications for in…

26 min
Data and discrimination: representing marginalised communities in data
The right to be counted, or the right to be left alone?
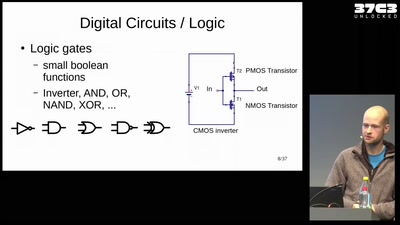
38 min
Place & route on silicon
A gentle introduction to place & route algorithms for…

26 min
Learning from embedded: less is more
...or how to use any existing SUSE OS variant to meet all…

43 min
Anykernels meet fuzzing
how to make NetBSD a better software for you and me
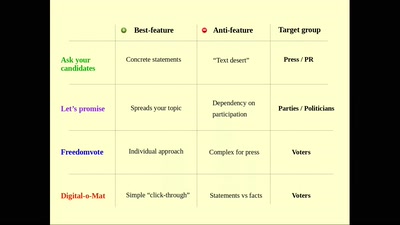
41 min
Ask your candidates and let everyone know about it
How to make use of democratic elections for your own purpose

53 min
Teaching machines new tricks
Machine learning: Silver bullet or route to evil?

30 min
A Torifying Tale
Our experiences of building and running Tor servers
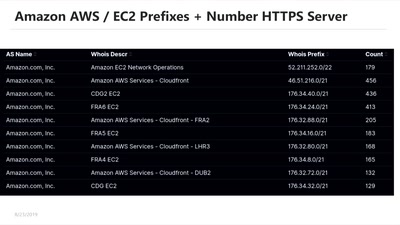
42 min
Fast Global Internet Scanning - Challenges and new Approaches
Or how to become your own ISP

48 min
(Web) Search on Linux driven sites
High speed search with SPHINX or MNOGO for huge amounts of…

59 min
Let Them Fail
An Introduction to Massively Distributed Finance or "Cloud…

39 min
DIY Survival
How to survive the apocalypse or a robot uprising

45 min
Further hacks on the Calypso platform
or how to turn a phone into a BTS
48 min
Testing a LiveCD? Igor is doing it.
or: How to make testing a distribution fun.
40 min
The first encrypted Steam Deck runs openSUSE
And yours should too!

32 min
