Search for "andy" returned 7349 results

49 min
MISP threat sharing platform
The MISP threat sharing platform is a free and open source…

38 min
Honey, let's hack the kitchen:
Attacks on critical and not-so-critical cyber physical…
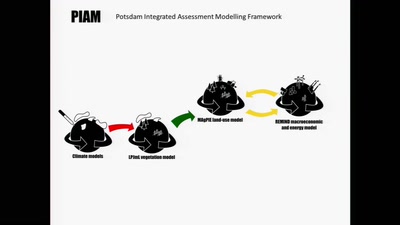
35 min
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

24 min
Security alerting made easy using Python
Sending real-time notifications to Discord and other…

31 min
openSUSE ALP prototype on AWS, experimental, but fun!
Experiences, challenges and how SUSE NeuVector came into…
28 min
Fleet Commander: The efficient way of managing the Desktop profiles of your fleet!
A brief description of the project and its internals!
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

40 min
Settling the IM war
Creating an open and federated protocol for instant…
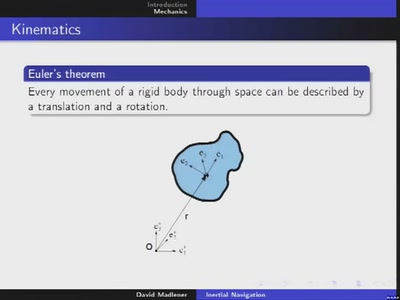
37 min
Inertial navigation
Rigid body dynamics and its application to dead reckoning

52 min
Adventures in Mapping Afghanistan Elections
The story of 3 Ushahidi mapping and reporting projects.

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP
49 min
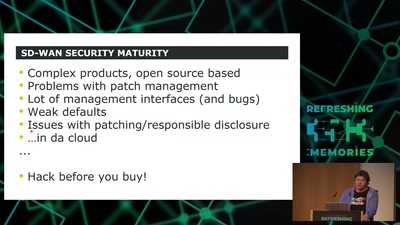
SD-WAN a New Hop
How to hack software defined network and keep your sanity?

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor

60 min
A brain is not a computer
Insights into neurology and psychological behaviours…

60 min
The Hash Disaster
Recent Results on Cryptanalysis and their Implications on…

62 min
GUERRILLA.COM
How to mess with media, the market and life itself

60 min
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…

49 min
Access to Knowledge
Copyright, Patents and Politics at the World Intellectual…

37 min
Eliminating the database bottleneck for proper horizontal scalability
Using embeddable databases to allow true and simple…
38 min
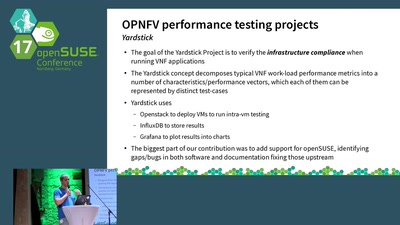
The importance of performance testing in the NFV world
Challenges and state-of-the-art in the OPNFV community
35 min
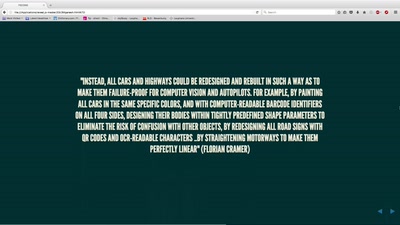
Ethics in the data society
Power and politics in the development of the driverless car

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

76 min
Information Operations
Sector-Oriented Analysis of the Potential Impact and…

100 min
