Search for "36c3" returned 2362 results
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

63 min
Reconstructing narratives
transparency in the service of justice
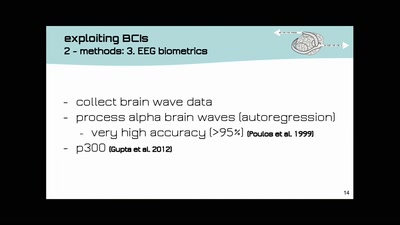
38 min
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…
38 min
T-Minus Zero
The first days in the life of the "Flying Laptop" satellite
132 min
Lightning Talks - Day 2
4 minutes of fame
37 min
Reverse-Engineering DisplayLink devices
USB to DVI for Hackers

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

32 min
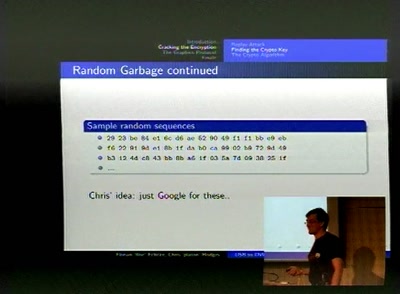
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
29 min
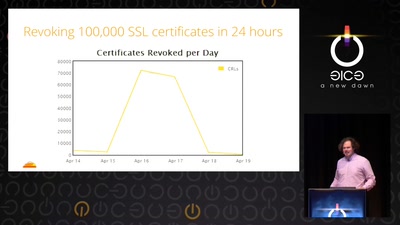
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…
32 min
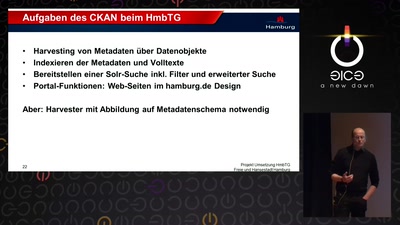
Das Transparenzportal Hamburg
Inhalt und Umsetzung

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…

60 min
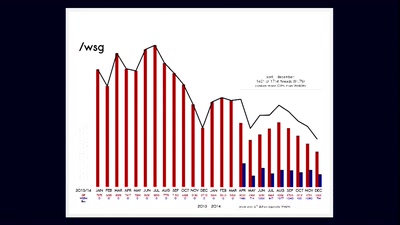
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age
31 min