Search for "338" returned 1978 results

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

32 min
History and implications of DRM
From tractors to Web standards
31 min
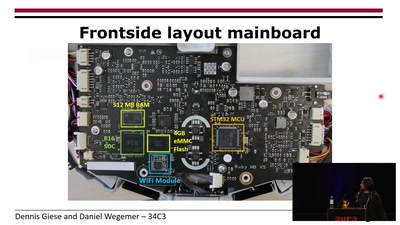
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

30 min