Search for "nook" returned 2101 results
61 min
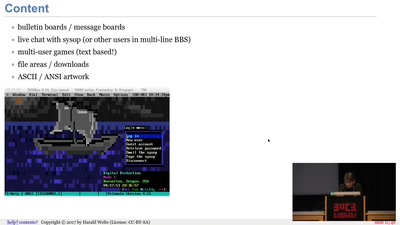
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

41 min
Why Railway Is Safe But Not Secure
Security Of Railway Communication Protocols

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

58 min
Virtual Machine Introspection
From the Outside Looking In

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild
29 min
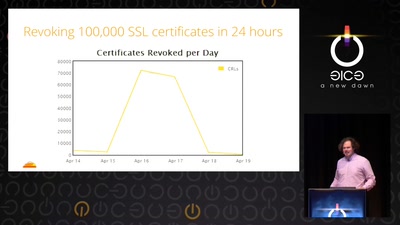
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…
61 min
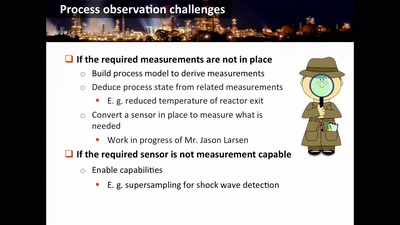
Damn Vulnerable Chemical Process
Exploitation in a new media

43 min
How Facebook tracks you on Android
(even if you don’t have a Facebook account)

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine
62 min
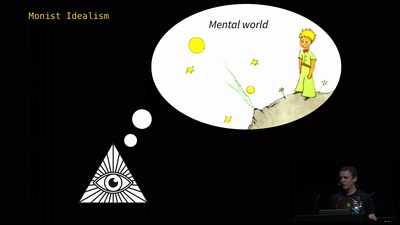
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul
60 min
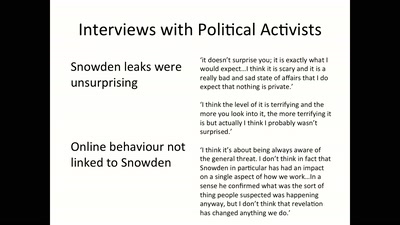
Media Coverage and the Public in the Surveillance Society
Findings from a Research Project on Digital Surveillance…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

55 min
How to Build a Mind
Artificial Intelligence Reloaded

59 min
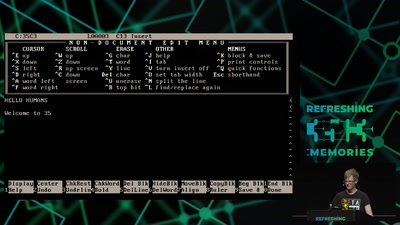
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
38 min