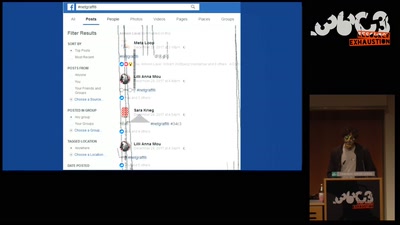
Search for "nook" returned 2101 results

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning

60 min
Hacking Reality
Mixed Reality and multi-sensory communication
40 min
Art against Facebook
Graffiti in the ruins of the feed and the…
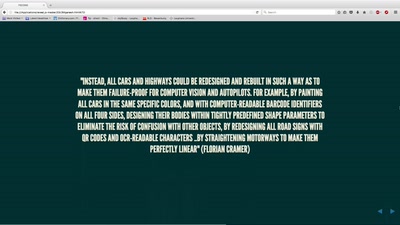
35 min
Ethics in the data society
Power and politics in the development of the driverless car

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

32 min
The Moon and European Space Exploration
Refocusing on the moon as a platform for future deep space…
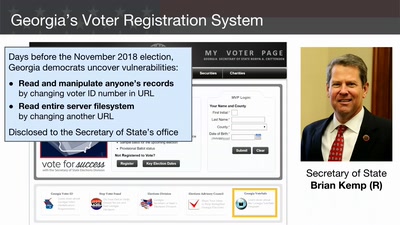
59 min
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

62 min
To Protect And Infect, Part 2
The militarization of the Internet

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…
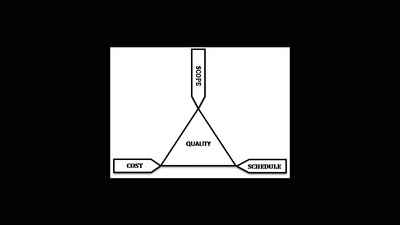
66 min
31C3 Keynote
A New Dawn
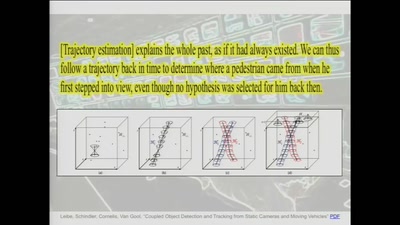
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition
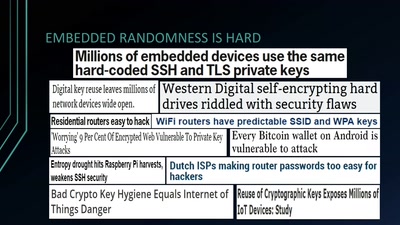
36 min
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

58 min