Search for "38c3" returned 2555 results

52 min
The engineering part of social engineering
Why just lying your way in won't get you anywhere
40 min
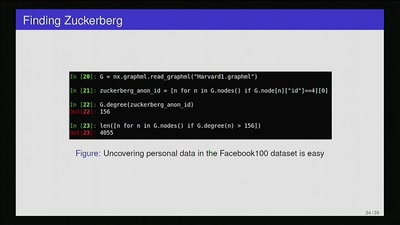
Privacy Invasion or Innovative Science?
Academia, social media data, and privacy

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes

49 min
Does Hacktivism Matter?
How the Btx hack changed computer law-making in Germany

59 min
Deceiving Authorship Detection
Tools to Maintain Anonymity Through Writing Style & Current…
60 min
What is WhiteIT and what does it aim for?
Why you probably want to be concerned about it and similiar…

55 min
Ein Mittelsmannangriff auf ein digitales Signiergerät
Bachelorarbeit Informatik Uni Kiel SS 2011

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…
56 min
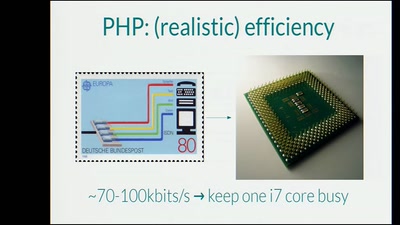
Effective Denial of Service attacks against web application platforms
We are the 99% (CPU usage)

59 min
Not your Grandfathers moon landing
Hell yeah, it's Rocket Science 3.1415926535897932384626!

128 min
Der Staatstrojaner
Vom braunen Briefumschlag bis zur Publikation
68 min
The future of protocol reversing and simulation applied on ZeroAccess botnet
Mapping your enemy Botnet with Netzob

61 min